Services
Technology Hardening
Our testing service simulates deep multi-vector DDoS attacks.

Volumetric attacks
Generating multi-gigabit attack traffic from multiple global locations, we test your ability to withstand extreme and sustained attacks
Application layer attacks
We overwhelm your web server tier with excessive HTTP/S GET or POST requests that test our resistance to resource exhaustion
Low-and- slow attacks
Using attacks such as lowLoris, R.U.D.Y., and SSL enegotiation, we test your ability to detect low resource attacks
A Structured & Controlled Process
Using a “white-box” test methodology, we analyze your entire network architecture and decide on the most relevant attack vectors to test

Planning Session
- Understand your network
architecture. - Define clear goals, attack vector
Controlled Attack
- Execute tests with 6-12 attack vectors
- Cover all attack categories (volumetric,
application-layer, low and slow)
Report & Analysis
- Deliver test results.
- Specify vulnerabilities and
reccomendations
DDoS Attack Simulator Platform
Our extensible testing platform executes DDoS attacks from bots distributed around the world. It sends real traffic using Web, DNS, and network attack vectors.
Get Actionable Recommendations
Following the DDoS Test, you receive a detailed report containing a full gap analysis outlining the main weaknesses, their severity, and how they should be fixed.
AWS DDoS Testing
Make sure your AWS deployment is secure with simulated DDoS attacks in a controlled environment.
Customized Testing
We help AWS customers verify their DDoS protection by simulating controlled attacks, providing detailed analysis, and making specific recommendations for improvement.
Our DDoS testing service, available to AWS Shield Advanced customers, is customized to match your AWS deployment architecture. So, whether you use EC2, ALB, ELB, Lamda, API Gateway or CloudFront–we’ll test the attack vectors that maximize valuefor your operational security.
Azure DDoS Testing
Ensure your Microsoft Azure deployment is secure with simulated DDoS attacks in a controlled environment.
Customized Testing
We help validate your DDoS protection and ensure your services or applications continue to function as expected during an attack. We provide simulated controlled DDoS attacks, accompanied by a detailed analysis, and specific recommendations for improvement.
Our DDoS testing service, available to customers with an Azure DDoS Protection Standard plan, is customized to match your Azure deployment infrastructure. So, whether you use Azure CDN, Azure Gateway, or Azure Virtual Machines–we’ll test the attack vectors to maximize the value of your testing.
Improve your
network architecture against attacks
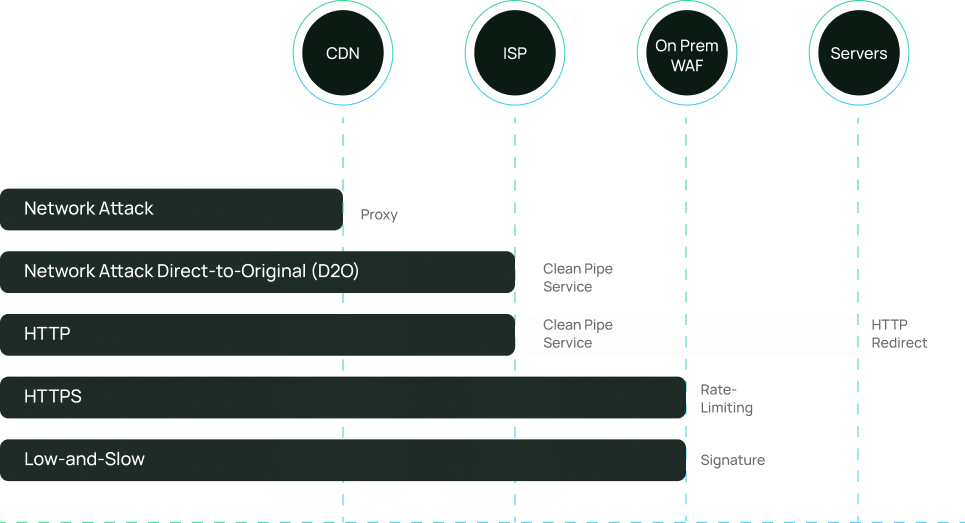
We identify which protection component will prevent each DDoS attack vector
Network Architecture
Our experts audit your DDoS network architecture infrastructure to identify weaknessess nd provide recommendations for maximizing DDoS protection. This step, taken regardless of which vendor you use, ensures a solid foundation for DDoS protection, with the right components in the right locations.

Attack Vector Analysis
We identify which protection component will prevent each DDoS attack vector.
Configuration Optimization
Installed DDoS protection solutions are often underutilized. Our team dives into your protection setup and provides detailed instructions on how to improve appliance configuration. For example, we ensure that rate limit thresholds are well-calibrated, that you have chosen the most appropriate web challenge, and that you fully utilize bot and geo-protection.
Get a Demo
Vendor Selection
An optional Red Button service includes methodical vendor evaluation, using a comprehensive RFP template. We then present our recommendations regarding several DDoS vendors with solutions most suitable for your needs, analyzing the pros and cons of each option.
Get a Demo
Heard enough? See it for yourself.
To learn how Algoritmik’s advanced infosec solutions can help you improve your information security posture, please schedule a demo.